Filters: Department: "Computing, School of" School Or College: "College of Engineering" Collection: "ir_uspace"
| Creator | Title | Description | Subject | Date | ||
|---|---|---|---|---|---|---|
| 126 |
 |
Thulasinathan, Aravindan; Pascucci, Valerio; Tierny, Julien | Topology Based Surface Meshing and Morphing | Morphing is a seamless transition from one image to the other, used in animation and motion pictures. Mesh Parameterization used in this process is a fundamental tool used for domain remeshing. In case of 2-manifolds for example, most approaches require that the input mesh be cut into one or mor... | 2010-10-06 | |
| 127 |
 |
Gopalakrishnan, Ganesh; Humphrey, Alan Parker; Derrick, Christopher Glade | An integration of dynamic MPI formal verification within eclipse PTP | Our research goals were to verify practical MPI programs for deadlocks, resource leaks, and assertion violations at the push of a button and be able to easily visualize the results. We also sought to integrate these capabilities with the Eclipse IDE via an Eclipse plug-in for the Parallel Tools Plat... | Verification; Graphical User Interfaces; Dynamic Interleaving Reduction; Message Passing; MPI; Multi-core; Eclipse Parallel Tools Platform; Trapeze Interactive Poster | 2010-03-15 |
| 128 |
 |
Balasubramonian, Rajeev | Staged reads: mitigating the impact of DRAM writes on DRAM reads | Main memory latencies have always been a concern for system performance. Given that reads are on the criti- cal path for CPU progress, reads must be prioritized over writes. However, writes must be eventually processed and they often delay pending reads. In fact, a single channel in the main memory ... | 2012-01-01 | |
| 129 |
 |
Regehr, John | Eliminating stack overflow by abstract interpretation | An important correctness criterion for software running on embedded microcontrollers is stack safety: a guarantee that the call stack does not overflow. Our first contribution is a method for statically guaranteeing stack safety of interrupt-driven embedded software using an approach based on contex... | 2005-01-01 | |
| 130 |
 |
Regehr, John | Evolving real-time systems using hierarchical scheduling and concurrency analysis | We have developed a new way to look at real-time and embedded software: as a collection of execution environments created by a hierarchy of schedulers. Common schedulers include those that run interrupts, bottom-half handlers, threads, and events. We have created algorithms for deriving response tim... | 2003-01-01 | |
| 131 |
 |
Regehr, John | Understanding integer overflow in C/C++ | Integer overflow bugs in C and C++ programs are difficult to track down and may lead to fatal errors or exploitable vulnerabilities. Although a number of tools for finding these bugs exist, the situation is complicated because not all overflows are bugs. Better tools need to be constructed-but a tho... | 2012-01-01 | |
| 132 |
 |
Regehr, John | Efficient memory safety for TinyOS | Reliable sensor network software is difficult to create: applications are concurrent and distributed, hardware-based memory protection is unavailable, and severe resource constraints necessitate the use of unsafe, low-level languages. Our work improves this situation by providing efficient memory an... | 2007-01-01 | |
| 133 |
 |
Regehr, John | HLS: a framework for composing soft real-time schedulers | Hierarchical CPU scheduling has emerged as a way to (1) support applications with diverse scheduling requirements in open systems, and (2) provide load isolation between applications, users, and other resource principals. Most existing work on hierarchical scheduling has focused on systems that prov... | 2001-01-01 | |
| 134 |
 |
Regehr, John | Efficient type and memory safety for tiny embedded systems | We report our experience in implementing type and memory safety in an efficient manner for sensor network nodes running TinyOS: tiny embedded systems running legacy, C-like code. A compiler for a safe language must often insert dynamic checks into the programs it produces; these generally make progr... | 2006-01-01 | |
| 135 |
 |
Chatterjee, Niladrish; Balasubramonian, Rajeev; Davis, Alan L. | Rethinking DRAM design and organization for energy-constrained multicores | DRAM vendors have traditionally optimized for low cost and high performance, often making design decisions that incur energy penalties. For example, a single conventional DRAM access activates thousands of bitlines in many chips, to return a single cache line to the CPU. The other bits may be access... | DRAM power consumption; Data-center power; Multicore memory; Trapeze Interactive Poster | 2010-03-15 |
| 136 |
 |
Johnson, Robert R. | Patterns of patterns | Purpose of this Poster is to demonstrate that it takes the patterns of values in all the many dimensions to place each patient in the final patterns shown in each of the 5 charts. The final patterns determine the ability of each technology to identify or distinguish patients in each class. It is p... | Gene patterns; Colon cancer; Trapeze Interactive poster | 2010-03-15 |
| 137 |
 |
Berzins, Martin | Adaptive high-order discontinuous galerkin solution of elastohydrodynamic lubrication point contact problems | This paper describes an adaptive implementation of a high order Discontinuous Galerkin (DG) method for the solution of elastohydrodynamic lubrication (EHL) point contact problems. These problems arise when modelling the thin lubricating film between contacts which are under sufficiently high pressur... | 2012-01-01 | |
| 138 |
 |
Li, Peng; Regehr, John | T-check: bug finding for sensor networks | A safety property is true if something bad never happens. If any state in an execution violates the safety property, the entire execution violates that property. A liveness property holds if something good will eventually happen. An execution satisfies a liveness property if the execution will en... | 2010-02-26 | |
| 139 |
 |
Regehr, John; Pagariya, Rohit Pannalalji | Direct equivalence testing | Testing embedded software is difficult. • Further complicated by presence of memory and type safety errors in software. • Compiler contain various known bugs. Developers are skeptical to upgrade the compilers. • Is your embedded software affected by memory safety and compilation erro... | ||
| 140 |
 |
Nguyen, Hoa Thanh; Nguyen, Thanh Hoang; Freire, Juliana | DeepPeep: A Form Search Engine | We present DeepPeep (http://www.deeppeep.org), a new search engine specialized in Web forms. DeepPeep uses a scalable infrastructure for discovering, organizing and analyzing Web forms which serve as entry points to hidden-Web sites. DeepPeep provides an intuitive interface that allows users t... | ||
| 141 |
 |
Regehr, John | Atomicity and visibility in tiny embedded systems | Visibility is a property of a programming language's memory model that determines when values stored by one concurrent computation become visible to other computations. Our work exploits the insight that in nesC, a C-like language with explicit atomicity, the traditional way of ensuring timely visib... | 2006-01-01 | |
| 142 |
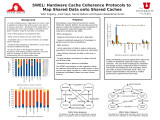 |
Pugsley, Seth H; Spjut, Josef Bo; Nellans, David W; Balasubramonian, Rajeev | SWEL: hardware cache coherence protocols to map shared data onto shared caches | In chip multiprocessors, replication of cache lines is allowed to reduce the latency each core has to access a cache line. Because of this replication, it is possible for one copy of data to become out of date if another copy of that data is modified. How a MESI protocol accomplishes this: ? K... | ||
| 143 |
 |
Regehr, John | Poster abstract: TinyOS 2.1 adding threads and memory protection to tinyOS | The release of TinyOS 2.0 two years ago was motivated by the need for greater platform flexibility, improved robustness and reliability, and a move towards service oriented application development. Since this time, we have seen the community embrace these efforts and add support for additional hardw... | 2008-01-01 | |
| 144 |
 |
Mates, Phillip Lopes; Silva, Claudio T. | crowdLabs: a provenance enabled web repository | The National Science Foundation Science and Technology Center for Coastal Margin Observation and Prediction (CMPO) is a multi-institutional center dedicated to coastal margins, which are regions consisting of very productive ecosystems that play an important role in global elemental cycles. CMPO ma... | CrowdLabs; Web repository; Coastal margins; Trapeze Interactive Poster | 2010-03-15 |
| 145 |
 |
Regehr, John | Eliminating the call stack to save RAM | Most programming languages support a call stack in the programming model and also in the runtime system.We show that for applications targeting low-power embedded microcontrollers (MCUs), RAM usage can be significantly decreased by partially or completely eliminating the runtime callstack. We presen... | 2009-01-01 | |
| 146 |
 |
Regehr, John | Precise garbage collection for C | Magpie is a source-to-source transformation for C programs that enables precise garbage collection, where precise means that integers are not confused with pointers, and the liveness of a pointer is apparent at the source level. Precise GC is primarily useful for long-running programs and programs t... | 2009-01-01 | |
| 147 |
 |
Gopalakrishnan, Ganesh | High level optimizations in compiling process descriptions to asynchronous circuits | Asynchronous/'Self-Timed designs are beginning to attract attention as promising means of dealing with the complexity of modern VLSI technology. In this paper, we present our views on why asynchronous systems matter. We then present details of our high level synthesis tool SHILPA that can automatic... | Self-timed; VLSI | 1992 |
| 148 |
 |
Gopalakrishnan, Ganesh | A general compositional approach to verifying hierarchical cache coherence protocols | Modern chip multiprocessor (CMP) cache coherence protocols are extremely complex and error prone to design. Modern symbolic methods are unable to provide much leverage for this class of examples. In [1], we presented a method to verify hierarchical and inclusive versions of these protocols using ... | Hierarchical cache coherence protocols; Verification | 2006-11-26 |
| 149 |
 |
Bennion, Scott Thomas | A method of solution for hydrodynamics and radiation diffusion as a multi-material problem in one dimension | Multi-material problem | 1971 | |
| 150 |
 |
Sobh, Tarek M.; Henderson, Thomas C. | URK: Utah robot kit - a three-link robot prototype | In this paper we will present the stages of designing and building a three-link robot manipulator prototype that was built as part of a research project for establishing a prototyping environment for robot manipulators. Building this robot enabled us determine the required subsystems and interfaces ... | URK; Utah robot kit; robot manipulator prototype; prototyping environment; robot manipulators; three-link | 1994 |
