|
|
Creator | Title | Description | Subject | Date |
| 1 |
 |
Eide, Eric Norman | Secure disk scrubbing in a large-scale automated testbed | | | 2010-02-26 |
| 2 |
 |
Kirby, Robert Michael | Kirby research group | | | 2012 |
| 3 |
 |
Johnson, Christopher R. | Optimizing Inverse Electrocardiographic Problem: Hybrid and High-Order Finite Element Method | One type of inverse problems in electrocardiography (ECG) is to non-invasively reconstruct epicardial electric potentials from body-surface measurements. We study how to design the finite element discretization of such problem, so as to optimize the conditioning and stability of the resulting num... | | |
| 4 |
 |
Widanagamaachchi, Wathsala Nayomi; Pascucci, Valerio | Image registration | Image Registration is the process of overlaying two or more images of the same scene, taken at different times, from different viewpoints and/or by different sensors. | | |
| 5 |
 |
Zhao, Lu; Regehr, John | Comparing program logics for reasoning about safety properties | To prove memory write and controls transfers do not interfere with other programs in embedded systems. Hoare Logic with Bale Predicate; Hoare Logic with Separation Conjunction. | | 2010-10-06 |
| 6 |
 |
Thulasinathan, Aravindan; Pascucci, Valerio; Tierny, Julien | Topology Based Surface Meshing and Morphing | Morphing is a seamless transition from one image to the other, used in animation and motion pictures. Mesh Parameterization used in this process is a fundamental tool used for domain remeshing. In case of 2-manifolds for example, most approaches require that the input mesh be cut into one or mor... | | 2010-10-06 |
| 7 |
 |
Gopalakrishnan, Ganesh; Humphrey, Alan Parker; Derrick, Christopher Glade | An integration of dynamic MPI formal verification within eclipse PTP | Our research goals were to verify practical MPI programs for deadlocks, resource leaks, and assertion violations at the push of a button and be able to easily visualize the results. We also sought to integrate these capabilities with the Eclipse IDE via an Eclipse plug-in for the Parallel Tools Plat... | Verification; Graphical User Interfaces; Dynamic Interleaving Reduction; Message Passing; MPI; Multi-core; Eclipse Parallel Tools Platform; Trapeze Interactive Poster | 2010-03-15 |
| 8 |
 |
Li, Guodong; Gopalakrishnan, Ganesh; Kirby, Robert Michael Ii | PUG : A Symbolic Verifier of GPU Programs | PUG is a automated verifier for GPU programs written in C/CUDA. PUG verifies GPU kernels for Data Races, Barrier mismatches, Totally wrong results, and Weak memory model related bugs. SMT-based correctness checking methods for these error are often more scalable, general and modular. | | 2010-10-06 |
| 9 |
 |
Chatterjee, Niladrish; Balasubramonian, Rajeev; Davis, Alan L. | Rethinking DRAM design and organization for energy-constrained multicores | DRAM vendors have traditionally optimized for low cost and high performance, often making design decisions that incur energy penalties. For example, a single conventional DRAM access activates thousands of bitlines in many chips, to return a single cache line to the CPU. The other bits may be access... | DRAM power consumption; Data-center power; Multicore memory; Trapeze Interactive Poster | 2010-03-15 |
| 10 |
 |
Johnson, Robert R. | Patterns of patterns | Purpose of this Poster is to demonstrate that it takes the patterns of values in all the many dimensions to place each patient in the final patterns shown in each of the 5 charts. The final patterns determine the ability of each technology to identify or distinguish patients in each class. It is p... | Gene patterns; Colon cancer; Trapeze Interactive poster | 2010-03-15 |
| 11 |
 |
Kasera, Sneha K.; Patwari, Neal | Mobility Assisted Secret Key Generation | Signature Based Key Generation. Wireless link signature; multiple paths caused by radio waves; their measurements are good signatures of links; link signatures measured almost symmetrically at two ends of wireless link, but cannot be measured from another location; use for secret key establishment;... | | |
| 12 |
 |
Joshi, Sarang; Venkatasubramanian, Suresh | Matching shapes using the current distance | Current Distance: It was introduced by Vaillant and Glaunès as a way of comparing shapes (point sets, curves, surfaces). This distance measure is defined by viewing a shape as a linear operator on a k-form field, and constructing a (dual) norm on the space of shapes. Shape Matching: Given two s... | | |
| 13 |
 |
Li, Peng; Regehr, John | T-check: bug finding for sensor networks | A safety property is true if something bad never happens. If any state in an execution violates the safety property, the entire execution violates that property. A liveness property holds if something good will eventually happen. An execution satisfies a liveness property if the execution will en... | | 2010-02-26 |
| 14 |
 |
Regehr, John; Pagariya, Rohit Pannalalji | Direct equivalence testing | Testing embedded software is difficult. • Further complicated by presence of memory and type safety errors in software. • Compiler contain various known bugs. Developers are skeptical to upgrade the compilers. • Is your embedded software affected by memory safety and compilation erro... | | |
| 15 |
 |
Musuvathy, Suraj Ravi; Cohen, Elaine | Tracing ridges on B-Spline surfaces | Won Best Paper Award at SIAM/ACM Joint Conference on Geometric and Physical Modeling, San Francisco, 2009 | | 2010-02-26 |
| 16 |
 |
Tripathi, Abhishek; Bremer, Peer-Timo; Pascucci, Valerio | Understanding global climate change | What is Climate Modeling? Use of quantitative methods to simulate the interactions of the atmosphere, oceans, land surface, and ice. Average Global Temperatures indicate a warming trend but that alone does not explain why it is happening. | | |
| 17 |
 |
Nguyen, Hoa Thanh; Nguyen, Thanh Hoang; Freire, Juliana | DeepPeep: A Form Search Engine | We present DeepPeep (http://www.deeppeep.org), a new search engine specialized in Web forms. DeepPeep uses a scalable infrastructure for discovering, organizing and analyzing Web forms which serve as entry points to hidden-Web sites. DeepPeep provides an intuitive interface that allows users t... | | |
| 18 |
 |
Kasera, Sneha K. | Enhancing covert communications with multiple colluding receivers | Traditional (single receiver) system setup: ? Choose exploit field (e.g. last byte of TCP Timestamp) ? Alice: probabilistically inject parts of coded message into field ? Bob: extract symbols from field, decode to correct errors ?Warden: assume full knowledge of system and keys Can we create un... | | 2010-10-06 |
| 19 |
 |
Grosset, Andre Vincent Pascal; Pascucci, Valerio | Infinite Zoom | Any image (apart from a fractal) has a finite resolution. On zooming in, we eventually see pixels. The aim of this project is to allow users to infinitely zoom in on an image. | | 2010-10-06 |
| 20 |
 |
Pascucci, Valerio | Morse theory and its application | Discussion of Morse Theory | Morse; Morse-Smale; Topology; Algorithms; Terrain; Analysis | |
| 21 |
 |
Kumar, Sidharth; Pascucci, Valerio | Remote visualization | Generalized Architecture and pipeline for a remote site | | |
| 22 |
 |
Fletcher, Preston Thomas; Moeller, John Henry; Phillips, Jeffrey; Venkatasubramanian, Suresh | Computing hulls in positive definite space | P(n): a Riemannian manifold Definition: symmetric positive-definite (n) (n) matrices Applications: Diffusion Tensor MRI (DT-MRI) Flow through voxel modeled in P(3) Elasticity Tensors Modeled by elements of P(6) Machine Learning Used in kernels Convex Hulls Data on P(n): Want to analyze... | | 2010-10-06 |
| 23 |
 |
Yang, Xuejun; Chen, Yang; Eide, Eric; Regehr, John | Finding compiler bugs with random testing | Undefined behavior (such as divide by 0) or unspecified behavior (such as order of evaluation) gives compilers freedom to diverge, causing failure to our voting mechanism Control Flow Analysis • a control flow analyzer that can handle abnormal edges created by jump statements (goto / break ... | | |
| 24 |
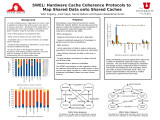 |
Pugsley, Seth H; Spjut, Josef Bo; Nellans, David W; Balasubramonian, Rajeev | SWEL: hardware cache coherence protocols to map shared data onto shared caches | In chip multiprocessors, replication of cache lines is allowed to reduce the latency each core has to access a cache line. Because of this replication, it is possible for one copy of data to become out of date if another copy of that data is modified. How a MESI protocol accomplishes this: ? K... | | |
| 25 |
 |
Gilbert, Nathan Alan; Riloff, Ellen M. | Exploring Knowledge-Rich Solutions to Noun Phrase Coreference Resolution | Coreference resolution is the task of identifying coreferent expressions in text. Accurate coreference resolution can improve other tasks such as machine translation, information retrievel and document summarization. Currently, the best approaches involve some form of supervised Machine Learni... | | |

























